protection
What is the 3-2-1-1-0 rule?
3
Independent copies
2
Different media
1
Copy off-site
1
Immutable or offline
0
Uncompromising data security.
Untouchable backup always secure and ready for restoration in 2 data centers in Poland.

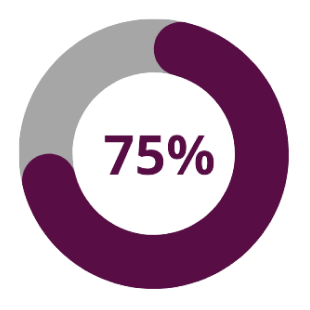 In 2023, as many as 75% of organisations fell victim to a ransomware attack, and the number of attacks increased compared to 2022. At the same time, as many as two-thirds of these organisations were attacked more than once.
In 2023, as many as 75% of organisations fell victim to a ransomware attack, and the number of attacks increased compared to 2022. At the same time, as many as two-thirds of these organisations were attacked more than once.
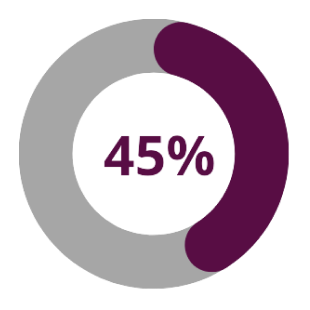 In the case of ransomware, an average of 45% of data is affected by an attack, meaning that nearly half of data and systems need to be recovered.
In the case of ransomware, an average of 45% of data is affected by an attack, meaning that nearly half of data and systems need to be recovered.
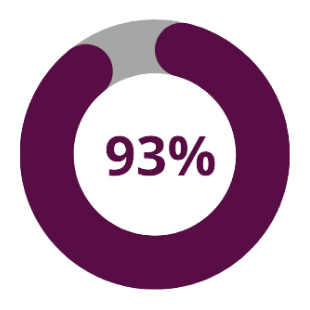 The majority, 93%, of attacks target local backup repositories. More than 76% of attacks on backup systems were successful.
The majority, 93%, of attacks target local backup repositories. More than 76% of attacks on backup systems were successful.
3
2
1
1
0
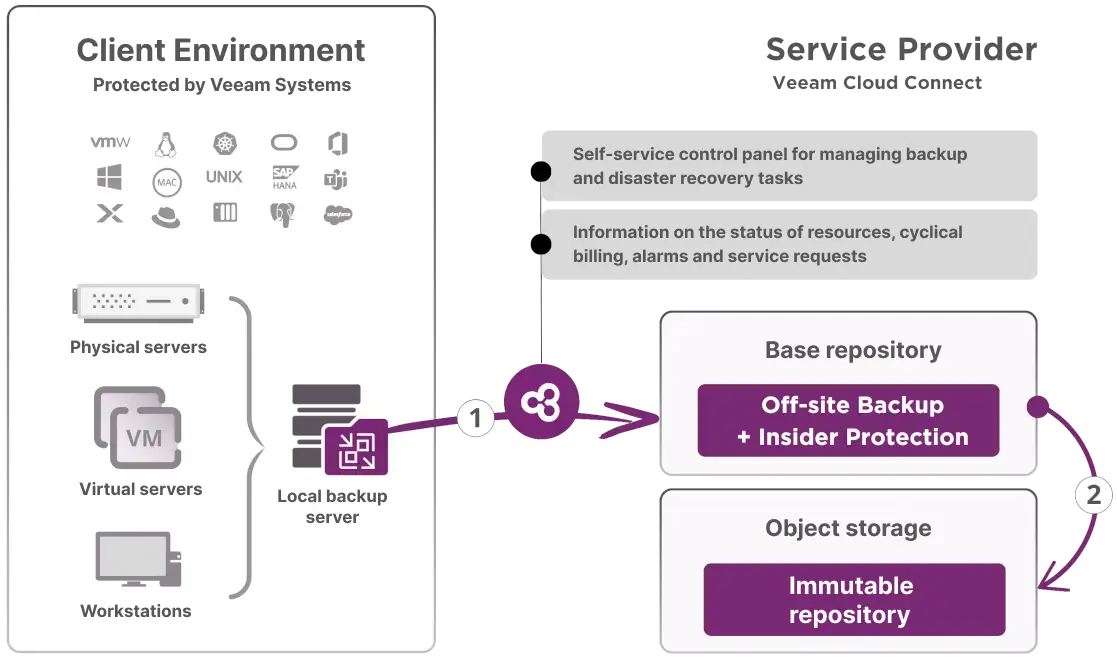







An off-site backup is an identical copy of a locally stored backup. Depending on the backup policy you adopt, you can either assume that every backup made will be sent to a remote repository or limit the backup copy task to the most important data. In summary, the space needed will be equal to the size of the local backup or some percentage of the repository depending on the decision of the customer's CIO.
The frequency of sending a backup to a remote location, i.e. off-site backup, should be closely related to the schedule of the backup job. Best practice is to execute a ‘backup copy job’ as soon as the backup job on the local repository is completed. It is also assumed that incremental backups should be executed at least once a day. This approach makes it easy to predict the RPO for different restore scenarios.
We currently provide two repositories for off-site backup and both are in Poland. The primary repository and object storage is located in the Korbank Data Center in Wrocław at 16K Fabryczna Street. The second centre, where we provide an IMMEDIATE cloud repository, is located in Radom.
The malicious code operates within the authentication domain to which it has gained access. It therefore encrypts repositories within a specific domain, including backups. However, there is no way for the attack to extend its reach into the Service Provider's environment. In the event of a targeted hack attack on the backup system in which administrative credentials are taken over, the hostile actor will be able to delete the backup jobs. However, the deleted backups will still remain in the service provider's system trash for 14 days. This ironclad reserve can be recovered manually by our admin team.
Recovery can take place using the local Veeam client, i.e. either the Veeam Backup & Replication or Veeam Agent level. The repository with backups on the Service Provider side is visible in the Veeam application. In the event that local resources are unavailable or have been encrypted by ransomware, restoration can be carried out using the Service Portal (VSCP), from which both files and entire images can be restored.
The test account has certain limitations. We limit the number of systems to 10 VM/Server/PC within one or multiple backup jobs. The total capacity of the repository for backups is 2TB. NOTE, you will need to have Veeam Backup & Replication or Veeam Agent to test the service. If you do not yet have an application from Veeam, you can download and install a trial version by registering on the manufacturer's website.